|
Hey there, Joseph here with some internal Secret Service emails. They show that even inside the agency, officials were clashing over whether they needed a warrant to use Locate X. Locate X is the tool I've covered a bunch, including its ability to track visitors to abortion clinics. Read below for why the Secret Service thinks you agreed to be tracked by accepting an app's terms of service. 📄 This article was primarily reported using public records requests. We are making it available to all readers as a public service. FOIA reporting can be expensive, please consider subscribing to 404 Media to support this work. Or send us a one time donation via our tip jar here. Officials inside the Secret Service clashed over whether they needed a warrant to use location data harvested from ordinary apps installed on smartphones, with some arguing that citizens have agreed to be tracked with such data by accepting app terms of service, despite those apps often not saying their data may end up with the authorities, according to hundreds of pages of internal Secret Service emails obtained by 404 Media. The emails provide deeper insight into the agency’s use of Locate X, a powerful surveillance capability that allows law enforcement officials to follow a phone, and person’s, precise movements over time at the click of a mouse. In 2023, a government oversight body found that the Secret Service, Customs and Border Protection, and Immigration and Customs Enforcement all used their access to such location data illegally. The Secret Service told 404 Media in an email last week it is no longer using the tool. “If USSS [U.S. Secret Service] is using Locate X, that is most concerning to us,” one of the internal emails said. 404 Media obtained them and other documents through a Freedom of Information Act (FOIA) request with the Secret Service.
This segment is a paid ad. If you’re interested in advertising, let's talk.

Generative AI (GenAI) chatbots are changing the way businesses engage with customers by providing intelligent, round-the-clock support. However, this technology comes with serious risks, including the potential for unsafe responses and the mishandling of sensitive requests, which can jeopardize a company’s reputation and customer safety.
In ActiveFence’s latest report, we explore these vulnerabilities via a case study from the travel industry to highlight broader implications for business using GenAI-powered applications. It also examines the challenges faced by travel companies, including risks to brand integrity and safety concerns related to user recommendations. Plus, we provide practical strategies for improving safety measures and protecting your GenAI applications from potential threats.
You’ll also find real-life examples of how our researchers manipulated the AI systems with risky prompts to reveal unsafe advice.
Stay informed and safeguard your business—read the full report today.
Locate X is made by a company called Babel Street. In October 404 Media, NOTUS, Haaretz, and Krebs on Security published articles based on videos that showed the Locate X tool in action. In one example, it was possible to follow the visitors to a specific abortion clinic across state lines and to their likely place of residence. Tools similar to Locate X often use data that has been collected from ordinary smartphone apps. Apps on both iOS and Android devices collect location data and then sell or transfer that to members of the data broker industry. Eventually, that data can end up in tools like Locate X. 💡 Do you know anything else about Locate X? I would love to hear from you. Using a non-work device, you can message me securely on Signal at +44 20 8133 5190. Otherwise, send me an email at joseph@404media.co. In early March 2020, tech publication Protocol first revealed the existence of Locate X. It reported that CBP, ICE, and the Secret Service were all using Locate X in some capacity. That article mentioned that Locate X’s terms specify that the tool should only be used for internal research purposes and cannot be used as evidence in a criminal case or mentioning the technology at all in legal proceedings. But this important limitation was news to some people included in the emails obtained by 404 Media. “I wasn’t aware of this,” one official wrote after reading the Protocol article. “This could conflict with discovery obligations in criminal proceedings.”  A screenshot from the emails. The Protocol report quoted a former Babel Street employee who said that the technology was used to crack down on credit card skimming. A document included in the emails says that the Secret Service can “utilize Babel Street’s Locate X to identify smartphones that were at multiple confirmed skimmed locations.” The internal emails also indicate which specific divisions inside the Secret Service may have turned to the technology. “It has been confirmed that our Protective Intelligence Division uses this product in its criminal investigations,” one March email written by a USSS Privacy Officer reads. As the name implies, the division’s mission includes protecting people and locations. Another email says that division was not using Locate X, but that the Office of Investigations Strategy may be. Another said that the Office of Investigations Strategy uses it “as an investigative tool.” One email shows that an official in the Secret Service wanted to use the tool to look for a phone in LaGuardia and Ft. Lauderdale airports. A third says that “Babel street locator” was used as part of Operation Crypto-Craig, a foreign fraud investigation. WARRANT OR NO WARRANTIn one March 2020 email, an official wrote that a part of the Department of Homeland Security was working on guidance around Locate X. That guidance said “Essentially that this tool is not strictly unlawful, but there are some limitations we should follow to improve our chances that it would be accepted by judicial review,” the email read. “We previously raised concerns to OGC [Office of the General Counsel] regarding the Department’s use of AdID tracking as it relates to the Supreme Court case Carpenter v. U.S,” another added, with AdID referring to the advertising identifier Locate X uses. That ruling decided that a mobile phone’s cell-site location data is protected under the Fourth Amendment and requires a search warrant to be accessed. In other words, this person was raising concerns that Locate X’s data could fall under that as well. 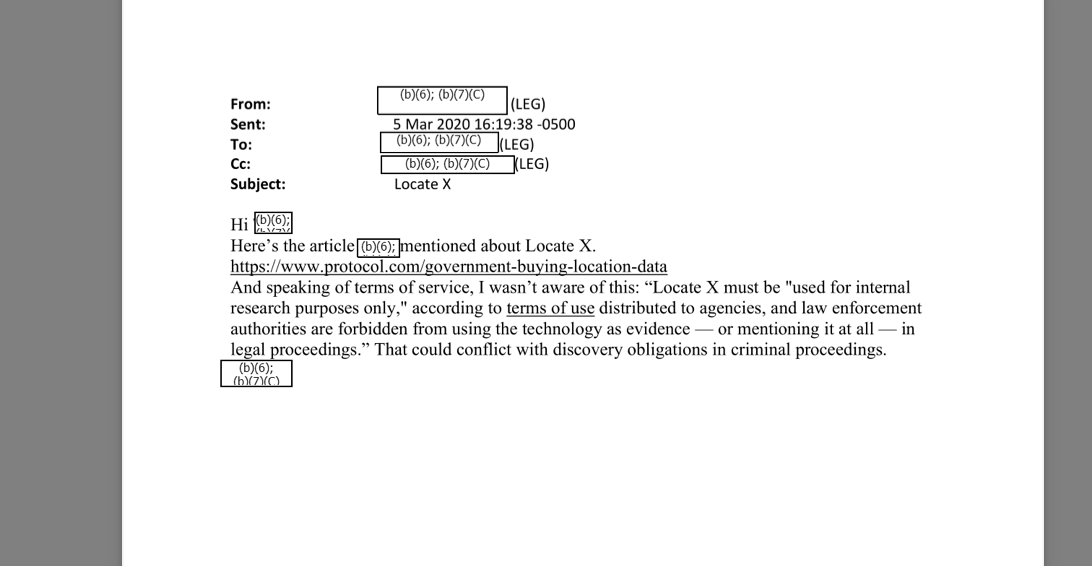 A screenshot from the emails. Babel Street itself took another stance, according to the emails. “I talked to Babel St[reet] execs tonight and their legal/privacy believes that Carpenter is not applicable,” one Secret Service email from 2018 reads. One reason was that Babel Street’s data is “opt in” only. “Users have to affirmatively agree for its collection and dissemination. It’s not passively collected without user knowledge,” the email read. “FYI. A warrant isn’t needed because the user gives consent. It happens when you agree to the terms of service,” another email reads. Of course, it is very unlikely that many people understand when they grant location data permissions to an ordinary app that their movements are going to be fed into a warrantless tracking system. I previously found that apps in similar data supply chains were not explicit with the context in which they were collecting user location data. In some cases, even app developers were not aware where they ultimately sent their users’ location data. Another reason Babel Street sees its data as not needing a warrant is because, according to the emails, it is “entirely anonymous because it’s hashed by Babel Street. It does not get you to end user.” That is not entirely true, either. In the demonstration of Locate X me and other journalists received recently, the tool allowed a user to lookup someone’s unique advertising identifier linked to their phone. And, the location data itself provided strong indicators of where someone lived or worked, making unmasking them trivial in many cases. 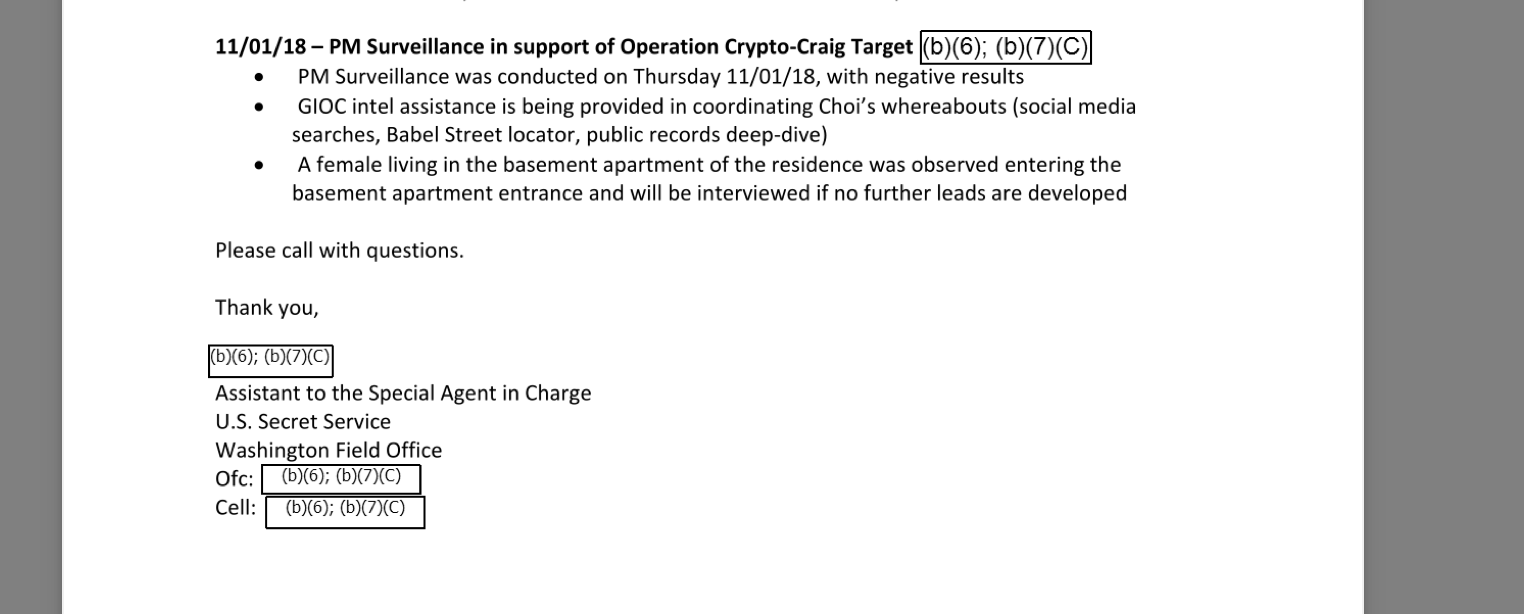 A screenshot from the emails. Regardless, some inside the Secret Service pushed back. “The means by which we are able to do that is different from the means used in Carpenter, but the outcome is essentially the same,” it reads. “I think the consent issue is the critical factor for this analysis, because Carpenter only applies when the individual had a reasonable expectation of privacy.” One email also took issue with characterization that Locate X’s data is “publicly available,” because “it’s definitely not open source.” “It seems questionable that the businesses who generate these location records would provide the location information directly to the government without a warrant, but they seel it to Babel Street who then sells it to us,” another read. Senator Ron Wyden told 404 Media in a statement that “I've long argued that the Trump administration memo blessing the government's warrantless purchase of Americans' location data wasn't worth the paper it was printed on and would never withstand real legal scrutiny. It’s not surprising to learn that even Secret Service officials raised concerns that this practice likely violated the Fourth Amendment.” “The Secret Service reportedly hid behind a flimsy claim that users consented to the sale of their location data, but even back in 2022 the agency told my office it hadn't bothered to actually verify this,” he added. “The Senate needs to pass my bipartisan Fourth Amendment is Not for Sale Act to set clear limits on when and how the government can use commercial information.” In an emailed statement, the Secret Service said the agency “uses a variety of tools as part of its protective and investigative operations and does so in accordance with applicable laws and government policies. Though we do not discuss the specific means and methods used during our operations, we can confirm that the Secret Service does not currently subscribe to this tool.” Responding to an article I previously wrote about the Secret Service’s use of Locate X, one August 2020 email included in the cache reads “I think we should stay quiet on it.”
|